Overview
CDP Wallets support Policies that enable developers to govern account and project behavior. Policies provide flexible configuration for enforcing controls based on transaction parameters such as destination address and transaction value.Use cases
- Wallet transaction filtering: Prevent transfers to known malicious or restricted addresses
- Allowlisted access to project features: Restrict access only to approved addresses to interact with a smart contract or mint a token
- Transaction limits per address: Limit financial risk by capping transaction values
- Prevent signing of fraudulent messages: Ensure compromised clients cannot prove control of your accounts
- USD Spend Limits: Restrict the amount in USD that can be sent, or approved, in a single transaction.
Policy field definitions
A policy is defined by the following fields:| Field | Description | Valid values |
|---|---|---|
scope | The level at which a policy gets applied | project or account |
rules | A list of rules that are used to govern the behavior of accounts | An array of rules |
action | The action to take when a policy is applied | accept or reject |
operation | The operation to perform when a policy is applied | signEvmTransaction, sendEvmTransaction, signEvmMessage, signEvmHash, signEvmTypedData, signSolTransaction, sendSolTransaction, signSolMessage, prepareUserOperation, or sendUserOperation |
criteria | The list of logical expressions that are evaluated to a transaction to determine whether a rule should be applied or not | An array of criteria. See API Reference for more details. |
Evaluation process
Aproject-level policy will be evaluated first, followed by any account-level policies. Read more technical details on policy evaluation in the API Reference documentation.
project-policy.json
How would this policy be evaluated?
How would this policy be evaluated?
In this example, the policy has two rules. An incoming transaction would be processed against each rule as follows:
- Accept any transaction with a value less than or equal to 1 ETH (expressed in Wei).
- Accept any transaction with a value less than or equal to 2 ETH, and an address in the allowlist.
- Transaction A with a value of 0.5 ETH
- Transaction B with a value of 2 ETH
- Transaction A would be accepted on the first rule, and the policy engine would stop evaluation against this policy.
- Transaction B would be processed against both rules. It would be rejected on the first rule, but accepted once processed against the second rule.
Supported operations
Each rule defines the behavior of a certainoperation. The operation corresponds to a CDP v2 API. Currently, the following operations are supported:
EVM Operations:
signEvmTransaction: To identify incoming signing transactions on an EVM compatible networksendEvmTransaction: To identify incoming signing transactions that are then sent to a supported networksignEvmTypedData: To identify incoming typed data to be signed by an accountsignEvmMessage: To identify incoming messages to be signed by an accountsignEvmHash: To identify incoming hash to be signed by an accountprepareUserOperation: For preparing user operations on a smart accountsendUserOperation: For sending user operations using a smart account
signSolTransaction: To identify incoming signing transactions on the Solana networksendSolTransaction: To identify incoming signing transactions that are then sent to the Solana mainnet or devnet network.signSolMessage: To identify incoming messages to be signed by a Solana account
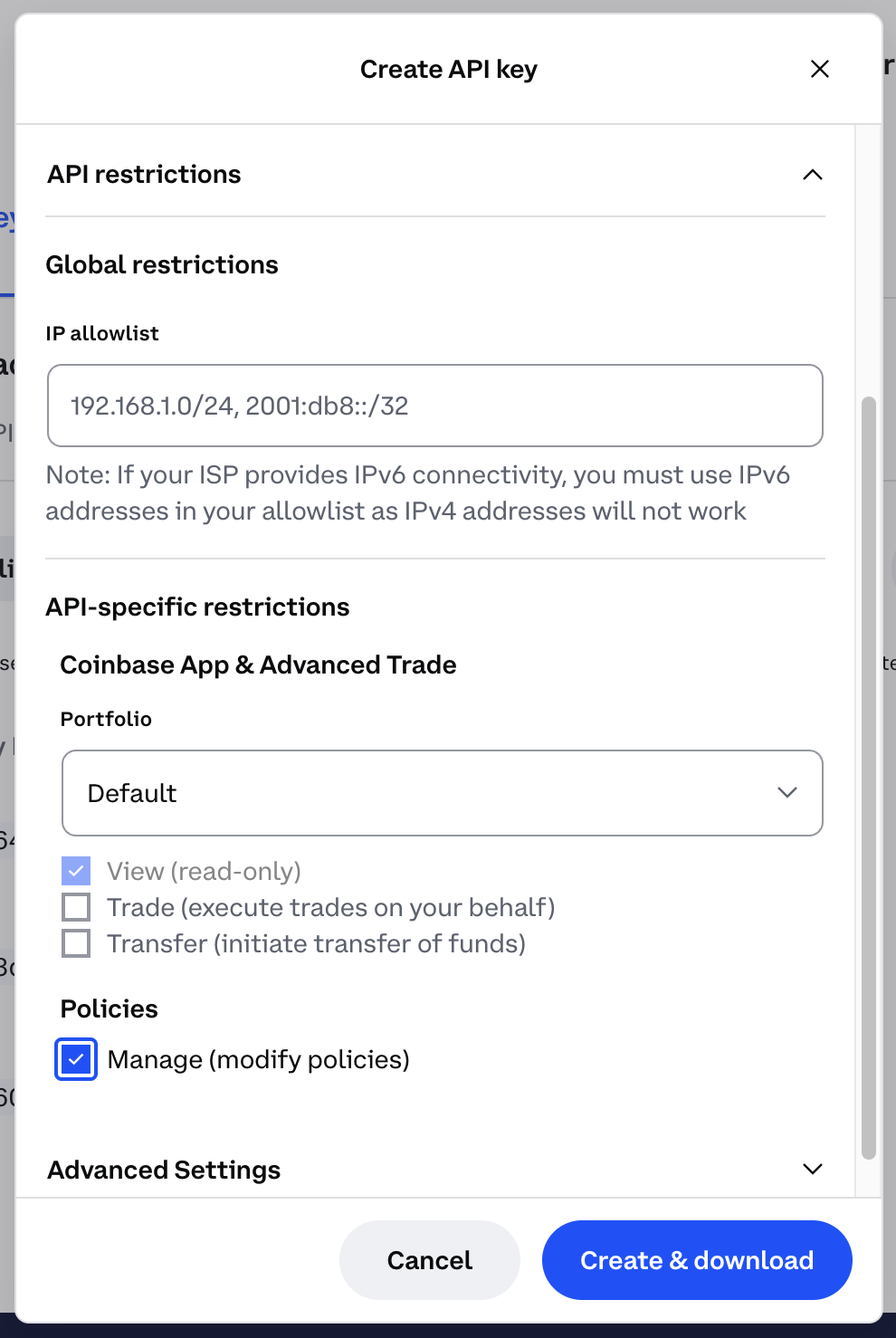
API Key Configuration
In order to securely manage Policies via API or SDK, you’ll need to manually configure an API key with a specific scope. This scope is required to perform the following API operations:- Create Policy
- Update Policy
- Delete Policy
- Account Policy assignment
Define a policy
Policies can be defined via CDP Portal UI or via the CDP SDK.You may only create one project-level policy per project.
UI (CDP Portal)
-
Navigate to Policies in the CDP Portal.
-
Click the Create new policy button to access the JSON editor. The modal will contain a sample policy that you can edit, but you can also use some of the examples in our EVM Policies or Solana Policies documentation.
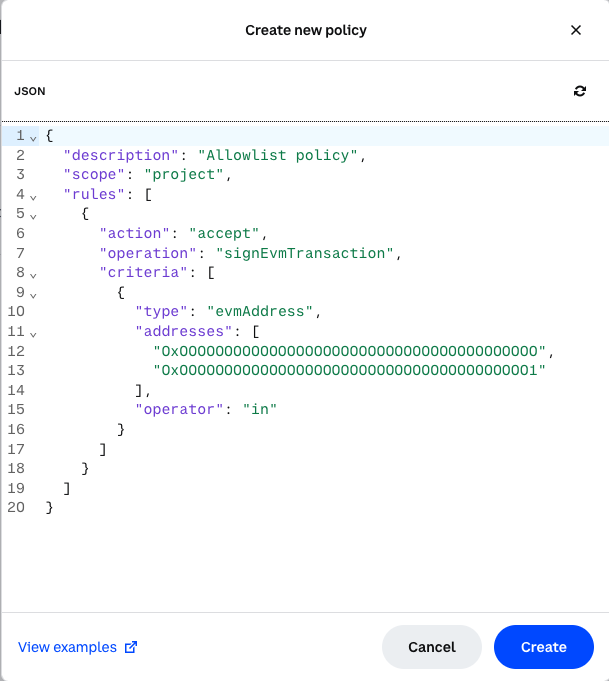
- Define the policy and click the Create button. If successful, you should see a “Policy created” message.
-
Refresh the page to see the new policy listed in the Policies dashboard:
Click the View button to edit or delete the policy.
- Account level policies should be added to the account programmatically via the SDK.
Programmatically
In order to manage Policies via SDK or API, you need to have an API Key with Policy management enabled
- Create an EVM account named
PolicyAccount - Create an account-level policy that only allows transactions less than or equal to 1 ETH to the address
0x000000000000000000000000000000000000dEaD - Apply the policy to the account we created
- Create another account named
OtherPolicyAccountwhich has the above policy applied during creation - Create a project-level policy that only allows transactions less than or equal to 5 ETH to the address
0x000000000000000000000000000000000000dEaD
A project-level policy is automatically applied to all accounts in the project on creation.An account-level policy may be applied to an account in 2 ways: during account creation, or after account creation by updating the account.
A project-level policy is automatically applied to all accounts in the project on creation.An account-level policy may be applied to an account in 2 ways: during account creation, or after account creation by updating the account.
- EVM Policies: Comprehensive examples for EVM-based transactions
- Solana Policies: Examples for Solana network transactions
Video: Watch and learn
Watch the video to learn how to implement and manage policies with CDP Server Wallet, which covers:- An overview of policy engine setup and configuration
- How to create project-level and account-level policies
- Best practices for implementing transaction controls and security measures
What to read next
- EVM Policies: Learn about EVM-specific policy examples and implementations
- Solana Policies: Learn about Solana-specific policy examples and implementations
- v2 Server Wallet Security: Learn more about the security features of the CDP v2 Server Wallet
- v2 API Reference: Explore the API reference for CDP Policies