EVMSolana
Overview
Custom authentication enables applications with existing authentication systems to integrate Embedded Wallets seamlessly. Instead of using CDP’s built-in authentication methods (email OTP, SMS, OAuth), you can use JSON Web Tokens (JWTs) from your own Identity Provider. This approach is ideal when:- You already have users authenticated via Auth0, Firebase, AWS Cognito, or a custom solution
- You want to implement single sign-on (SSO) across your entire platform
- You need to integrate with corporate identity systems
- You must use specific authentication providers for regulatory compliance
How it works
Custom authentication follows a straightforward flow that leverages your existing identity infrastructure:Pre-authentication setup
Pre-authentication setup
Before users can authenticate, you configure your JWKS (JSON Web Key Set) endpoint in the CDP Portal. This allows CDP to verify the authenticity of JWTs issued by your Identity Provider.
Authentication flow
Authentication flow
- User logs in: The user authenticates with your existing authentication system (Auth0, Firebase, etc.)
- JWT generation: Your Identity Provider generates a valid JWT for the authenticated user
- CDP integration: Your application provides the JWT to CDP via the
customAuth.getJwtcallback - JWT validation: CDP retrieves your JWKS endpoint (configured in Portal), validates the JWT signature, and checks required claims (
iss,exp,iat, and your configured user identifier claim) - Wallet access: Upon successful validation, CDP uses the configured claim (default:
sub) to uniquely identify the user and get or create their embedded wallet
Session management
Session management
Unlike CDP’s built-in authentication, custom auth sessions are managed entirely by your Identity Provider:
- CDP always requests a fresh JWT via the
getJwtcallback when needed - Token refresh is handled by your IDP, not CDP
- Session duration is controlled by your IDP’s configuration
- Users only need to sign out from your IDP
Prerequisites
Before implementing custom authentication, ensure your Identity Provider supports:- JWKS (JSON Web Key Sets) with RS256 or ES256 signing algorithms
- Required JWT claims:
iss(issuer): Your Identity Provider’s domainsub(subject): Unique identifier that identifies the particular user on your application (default, but configurable - see User Identification)exp(expiration): Token expiration timestampiat(issued at): Token issuance timestamp
1. Choose how to identify users
CDP uses a specific claim from your JWT to uniquely identify users and associate them with their embedded wallets. By default, CDP uses the standardsub (subject) claim, but you can configure an arbitrary JWT claim to serve as the user identifier.
Default claim
If you don’t specify a custom user identifier claim, CDP will use the JWT’ssub claim:
Custom claim
You can configure CDP to use an arbitrary claim in your JWT as the user identifier. Common alternatives include:Email address
Email address
Useful when email is the primary identifier in your system:When to use: Your users primarily identify themselves by email, and emails are stable/don’t change.
Username
Username
Useful when usernames are the primary identifier:When to use: Your application uses stable usernames as the primary identifier.
Custom user ID
Custom user ID
Useful when you have your own internal user ID system:When to use: You have an internal user ID that’s stable and want to maintain consistency with your existing systems.
Best practices
- Use the default
subclaim unless you have a specific reason to use a different claim - Avoid claims that users can change (like display names or mutable usernames)
- Test your configuration thoroughly before going to production
- Valid claim name examples:
email,username,user_id,external_id - Invalid claim name examples:
Email(uppercase),user-id(dash),user.id(dot)
2. Configure CDP Portal
To configure custom authentication in the CDP Portal:Navigate to your project
Go to the CDP Portal
Locate custom authentication settings
Find custom authentication settings under your project configuration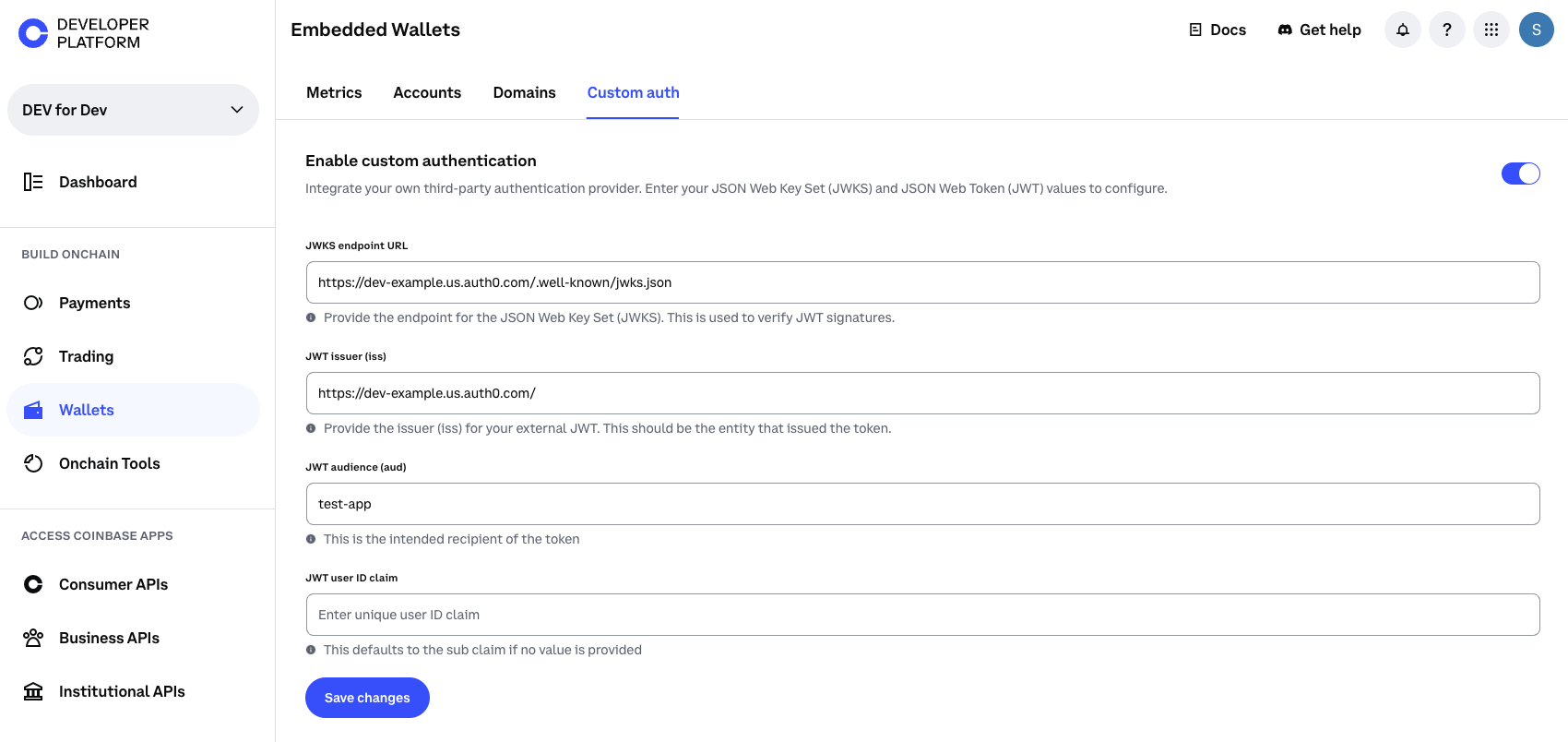

Add your JWKS endpoint URL
For example:
https://YOUR_DOMAIN.auth0.com/.well-known/jwks.json if using Auth0Configure expected claims
- Issuer (
iss): Your Identity Provider’s domain (required) - Audience (
aud): Your API or app identifier
Configure user identifier claim (optional)
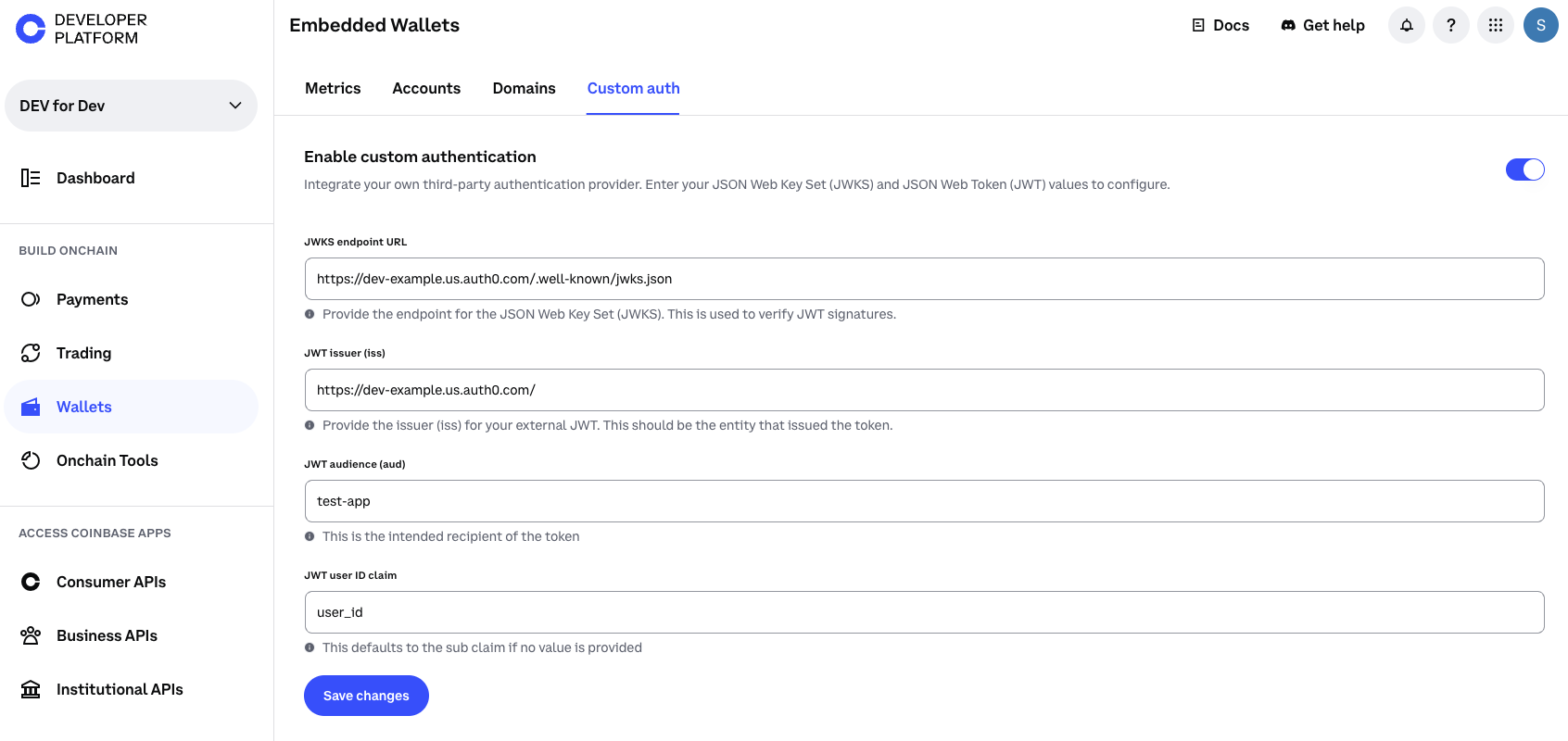
- User Identifier Claim: Which JWT claim to use for identifying users
- Default: If left empty, CDP uses the standard
subclaim - Examples:
email,username,user_id,external_id - Validation: Must start with a lowercase letter, only lowercase letters and underscores
- CDP verifies this claim exists and is non-empty during authentication
3. Integrate the SDK
The CDP Frontend SDK provides built-in support for custom authentication through thecustomAuth configuration option.
React
For React applications, useCDPHooksProvider or CDPReactProvider with the customAuth configuration:
Non-React
For vanilla JavaScript/TypeScript or other frameworks, use theinitialize method from @coinbase/cdp-core:
The
getJwt callback is called automatically by CDP whenever authentication is needed. It should return a fresh JWT from your Identity Provider or undefined if the user is not authenticated.4. Implement auth flow
Once you’ve configured custom authentication, you need to explicitly authenticate the user with CDP after they log in with your Identity Provider.Triggering auth
After your user logs in with your IDP (Auth0, Firebase, etc.), callauthenticateWithJWT() to authenticate with CDP:
- First-time users: CDP will create a new embedded wallet for the user (based on the configured user identifier claim, defaulting to
sub) - Returning users: CDP will retrieve their existing wallet (using the same user identifier claim value)
Accessing wallet data
Once authenticated with CDP, you can access the user’s wallet:Monitoring auth state
Use theuseIsSignedIn hook to monitor authentication state:
5. Test and debug
Verify JWT structure
Before integrating with CDP, verify your JWT contains the required claims:- Obtain a JWT from your Identity Provider
- Decode it using jwt.io or similar tool
- Verify claims:
iss: Matches your configured issueraud: Matches your configured audienceexp: Token expiration is in the futureiat: Token issuance timestamp- User identifier claim: Contains a unique, stable user ID
- If using default: Verify
subclaim exists - If using custom claim: Verify your configured claim (e.g.,
email,user_id) exists and is non-empty
- If using default: Verify
sub claim:
email claim as user identifier:
Validate JWKS endpoint
Ensure your JWKS endpoint is accessible and returns valid keys:- Access your JWKS URL in a browser (e.g.,
https://example.auth0.com/.well-known/jwks.json) - Verify the response contains public keys
Session management
Custom authentication sessions differ from CDP’s built-in authentication in several key ways:Token lifecycle
- Managed by your Identity Provider: Session duration, token expiration, and refresh are controlled by your Identity Provider
- Always fresh: CDP calls
getJwtwhenever it needs authentication, ensuring tokens are always current - No CDP refresh: CDP does not store or refresh tokens, it relies entirely on your
getJwtcallback - Maximum TTL: JWTs must have an expiration time (
exp) within 7 days from issuance
Sign out
When using custom authentication, signing out from your Identity Provider is sufficient:Complete example
For a complete working implementation of custom authentication with Auth0, see our example application React Custom Auth Demo App.What to read next
- Authentication Methods: Overview of all authentication options
- Session Management: Understanding session lifecycle with custom auth
- Implementation Guide: General authentication implementation patterns
- Security Configuration: Configure domain allowlisting
- Best Practices: Security recommendations and production readiness