Generating a JWT
Regardless of which code snippet you use, follow these steps:- Replace
key nameandkey secretwith your key name and private key.key secretis a multi-line key and newlines must be preserved to properly parse the key. Do this on one line with\nescaped newlines, or with a multi-line string. - Update the
request_pathandrequest_host or urlvariables as needed depending on which endpoint is being targeted. - Run the generation script that prints the command
export JWT=.... - Run the generated command to save your JWT.
Code samples for Ed25519 Keys
These code samples are for Ed25519 Signature algorithm keys.- JavaScript
- TypeScript
- Python
- Go
- Ruby
- PHP
- Java
- C++
- C#
First, install the CDP SDK:Create a new file for JWT generation code:Finally, run the script to generate the JWT output and export it as an environment variable:
main.js
Code samples for ECDSA Keys
ECDSA is a legacy key algorithm. You should use Ed25519 instead. Choose ECDSA only when required by the Coinbase App SDK or Advanced Trade SDK.See product compatibility for details.
- Python
- JavaScript
- TypeScript
- Go
- Ruby
- PHP
- Java
- C++
- C#
First, install the CDP SDK:Create a new file for JWT generation code:Finally, run the script to generate the JWT output and export it as an environment variable:
main.py
Using a JWT
Use your generated JWT by including it as a bearer token within your request:Shell
Shell
Learn More about JWTs
JWTs are a secure method of authenticating API calls, especially crucial for platforms handling sensitive financial information. They combine encryption and access management in a single token, offering a robust security layer compared to traditional API keys. At Coinbase, upholding our motto “The most trusted name in Crypto” means ensuring the utmost security in every aspect of our operations. As digital threats evolve, so must our methods of safeguarding user data. This is why we employ JSON Web Tokens (JWTs) for API authentication—a format that not only verifies identity but also encrypts critical information within a secure token framework.What is a JSON Web Token (JWT)?
A JSON Web Token (JWT) is a compact, URL-safe means of representing claims to be transferred between two parties. At Coinbase, JWTs encapsulate the claims in a JSON object that can be digitally signed or encrypted. Each JWT consists of three parts: the Header, the Payload, and the Signature. We’ll dive deeper into each of these below.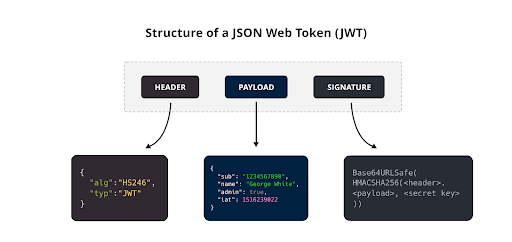
The Anatomy of a JWT
Understanding the structure of a JSON Web Token (JWT) is key to leveraging its full potential for secure API interactions. A JWT consists of three distinct parts:- Header: This section declares the type of the token, JWT, and the algorithm used for the signature, such as ES256 in Coinbase’s case, which are critical for ensuring the security and integrity of the token.
- Payload: Containing claims such as the user’s identity, role, and token expiration time. At Coinbase, this data is crucial for enabling not just authentication but also for ensuring that each transaction aligns with our user’s privileges and security requirements.
- Signature: The final component is a cryptographic signature that verifies that the token comes from a trusted source and has not been altered. This ensures that the transaction is both secure and verifiable. This structure not only ensures compliance with rigorous security standards but also supports transparent and trustworthy transactions across our platform.
Why Use JWTs for API Authentication?
In the realm of financial transactions, where security cannot be compromised, JWTs offer a sophisticated method for authenticating API calls that goes beyond traditional approaches. At Coinbase, our commitment to being “The most trusted name in Crypto” necessitates a framework that not only enhances security but also efficiently handles the scale and complexity of modern financial systems. JWTs excel in this environment due to several key features:- Improved Security Features: JWTs provide a robust mechanism for ensuring data integrity and authenticity. By using advanced algorithms for signatures, each token is secured against tampering, crucial for protecting sensitive financial data.
- Stateless Nature: Unlike session-based authentication, JWTs do not require server-side storage to verify each request. This statelessness enables our systems to scale dynamically without the overhead of session management, critical in handling high volumes of transactions seamlessly.
- Detailed Control Over User Permissions and Token Expiration: JWTs contain detailed claims that specify user roles and access privileges, allowing for fine-grained access control. Furthermore, token expiration is explicitly managed within the JWT, ensuring that permissions are timely and securely revoked when necessary.
When dealing with APIs across different environments or with multiple endpoints, it’s wise to extract and verify each component of the URI:
- HTTP Method: Ensure it matches the requirements (e.g., GET, POST).
- Host: Check if it corresponds to the correct API server (e.g., api.coinbase.com, api.developer.coinbase.com).
- Endpoint Path: Verify the path that corresponds to the specific API functionality you need (e.g., /api/v3/brokerage/accounts).
Common Pitfalls and How to Avoid Them
- Dynamic Parameters: Passing the HTTP method, and the correctly formatted URL domain and URL path. This would require the variables assigned to these parameters to be dynamic in nature and to be set, at runtime to the API endpoint being queried.
- Token Expiration: manage the token expiration to a timeframe which makes sense for your use-case (ie. adding more time for latency if using a proxy.) For reference, our samples all set the expiration to 120 seconds, or 2 minutes.
- Format and Import API Keys: keep original key formatting and import both the name and private key appropriately into the JWT creation file. If running into authentication issues after following all the above steps, consider adding debugging to see what the actual private key and key name resolve to at runtime.
- Clock Skew Issues: JWTs depend on synchronized timestamps for
nbf(Not Before) andexp(Expiration) claims. Even small discrepancies between server and client clocks can cause tokens to be rejected. Ensure systems are synchronized using a reliable time source, such as NTP. - Improper Header Configuration: Ensure the JWT header includes the correct
alg(Algorithm) andkid(Key ID). Misconfigurations can result in failed verifications. Follow Coinbase guidelines to set these fields accurately. - Payload Bloat: Avoid adding unnecessary data to the JWT payload. Overloading the payload can increase token size, leading to performance issues and potential exposure of sensitive information. Include only essential claims needed for the specific API request.
Further JWT related reading:
- Official JWT documentation
- JWT.io debugging tool